API Management Strategies for Security and Compliance
In today’s rapidly evolving digital marketplace, APIs have become integral to delivering real-time connected user experiences. However, their true success hinges on ensuring end-to-end data security and compliance. With their widespread use, evident in over 24,000+ API registrations on ProgrammableWeb and more than 3 million API repositories on GitHub, finding methods and tools to manage these technical assets has become a key concern for many businesses.
Incorporating APIs alone is not enough. Effective API management is critical for ensuring enterprise wide visibility, security, and stringent supervision. So, the question arises: how do you effectively manage API and drive business growth without compromising security and regulatory standards?
This article will explore how these solutions enhance APIsecurity, followed by strategies to strengthen them efficiently.
Understanding APIs and Their Role in Security
API, an acronym for Application Programming Interface, is a group of protocols and rules that allows software applications to communicate and share data. Through effective API management, organizations can aptly build and market new applications, control functionality, iterate quickly, and effectively keep up with the changing customer needs. Moreover, clear interfaces for data exchange through APIs help you minimize the risk of errors, fraud, and malicious threats.
The Need for API Management Solutions
While developing, integrating, and monitoring your APIs is crucial, effective API management goes beyond just deploying APIs. It involves a strategic approach to audit, support, and update them. With 45% of IT executives highlighting the significance of API governance, the role of API Management Solutions becomes indispensable.
API Management Solutions for Enhancing Security
API management solution involves a suite of tools, processes, and policies to address the above critical elements throughout the API lifecycle. When executed effectively, these tools empower you to control who can access your data and APIs, providing complete authority over your resources, internally and externally. Additionally, they allow you to enhance service capabilities and product functionalities for end-users, business partners, and employees without disrupting service continuity, all while adhering to security and regulatory requirements.
API Security and Key Considerations within API Management Solutions
What is API Security?
API security is the process of protecting your application program interfaces (APIs) from threats, misuse, unauthorized access, and vulnerabilities. API Management Solutions plays a pivotal role in supporting this process.
Why does API security matter?
As previously stated, APIs enable your applications to talk to each other effectively; thus, securing them is critical, as it involves large databases. If you’re not aware of the scope of its impact, data breaches can cost you huge penalties, litigation, and, most of all, customer trust. Studies uncover at least three API-related data breaches in the last two years, reported by 74% of respondents, which indicates an absolute need for enhanced API security measures.
Before we look into the API security measures, it is critical to understand what you need to protect your APIs from.
API Vulnerabilities You Should Be Wary Of
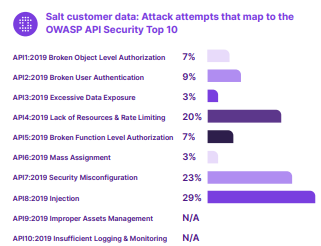
The Open Web Application Security Project (OWASP), a globally recognized foundation for generating standardized application security awareness, enlists the following vulnerabilities that pose serious threats to web applications and APIs. Let’s take a closer look at each of these below:
- Broken Object Level API Authorization: Inadequate checks in API endpoints expose sensitive data via object identifiers, leading to access control issues and making it more prone to being exposed to individuals without access.
- Broken API Authentication: This is similar to having a faulty lock on a door. If the authentication mechanisms(or lock) are weak, attackers can impersonate users and gain access to your protected information, compromising individual and enterprise API security.
- Excessive Data Exposure Through APIs: If an API shares too much data and relies on the app or user to filter it, chances are it may expose sensitive information unnecessarily.
- Lack of Resources and Rate Limiting: An absence of limits on resource requests can cause system overload, degrading server performance and making it vulnerable to attacks like DoS and brute force.
- Broken Function Level Authorization: An API with unclear role distinctions and complex access control policies might grant unauthorized users access to restricted functions and resources. This is similar to mistakenly allowing access to exclusive VIP areas to individuals who aren’t subscribed for such privileges.
- Mass Assignment: If an API binds client-supplied data directly to data models without filtering, it enables attackers to modify unintended object properties without being noticed.
- Security Misconfiguration: Common setup errors like insecure defaults, open storage, ad-hoc configurations, and misconfigured headers can leave your APIs vulnerable to attacks.
- Malicious API Injection Threats: Attackers can execute unauthorized commands or access data by injecting malicious code into an API request, leading to risks of data breach, data corruption, or entire system takeover.
- Improper Assets Management: Unlike other API risks, this risk stems from human error and oversight. It refers to inadequate management and documentation of API versions, unpatched API endpoints still connected to the database, missing or outdated host inventory, and unclear ownership of API endpoints. It is crucial to note that safeguarding APIs goes beyond production APIs; instead, you must ensure complete protection of several other APIs, including Public APIs (or external APIs), Internal APIs, Partner APIs, Third-Party APIs, and Composite APIs.
- Insufficient API Logging and Monitoring: Lack of detailed logging and monitoring allows undetected data breaches, delaying detection and response.
Although APIs are susceptible to each of the above risks, research uncovered the top three API security risks to be Simple Injection Attacks (29%), followed by Security Misconfiguration (23%), and Lack of Resources and Rate Limiting issues (20%).
How API Management Solutions Enhance Your API Security
Securing APIs is essential to leverage its benefits in the digital space. Following are some of the ways API management solutions empower you to strengthen API security and boost your defense against evolving threats:
Authenticate and Authorize:
- Implement robust authentication protocols such as OAuth2, JWT (JSON Web Tokens), or API keys within your API Management Solution. These mechanisms control access to APIs, ensuring only authorized users can interact with your API.
- Make sure the API access is strictly based on the principle of least privilege (POLP).
- Consider enabling a two-factor authentication to add an extra layer of security.
Implement Access Control:
- Adopt a zero-trust security model, a cornerstone of modern API Management Solutions. These tools are designed to ensure no request is trusted by default, regardless of its origin within the network. This approach not only enhances security but also facilitates secure access to internal data for third parties.
- Use firewalls or API gateways to manage access and protect against unauthorized entry. Integrate Rate Limiting:
- Integrate rate limiting to prevent potential security threats like brute force and denial-of-service (DoS) attacks. This ensures your API remains available and responsive to legitimate users and prevents abuse by limiting how many requests a user can make in a given time frame. • Employ geo-velocity checks to validate access legitimacy based on location and speed of travel.
Encrypt Requests and Responses:
- Always transmit data over secure HTTPS/SSL protocols. Apply HTTP Strict Transport Security (HSTS) where possible to enforce secure connections.
- Ensure you’re using upgraded versions of SSL/TLS protocols.
Validate the Data:
- Implement rigorous server-side data cleaning and validation to prevent common security issues like SQL injection and cross-site request forgery (CSRF) attacks. This involves checking, sanitizing, and validating all incoming data before processing.
Assess API Risks:
- Perform regular risk assessments against standards like OWASP's API Security Top 10. • Document and update assessments whenever the API changes.
Share Only Necessary Information:
- Ensure API responses contain only the data needed for the request to minimize the risk of data leakage.
Record APIs in an API Registry:
- Keep a comprehensive registry of all your APIs (API functionality, usage, access controls, and ownership) to avoid undocumented or shadow APIs for robust compliance and security management.
Conduct Regular Security Tests:
- Continuously test live APIs to identify and rectify security vulnerabilities.
- Have a responsive incident management plan to promptly address API security breaches and attack alerts.
Securely Manage API Keys:
- Store API keys securely, avoid embedding them in code, use secrets management services for storage, and regularly rotate these keys to mitigate the risk of unauthorized access.
Add AI to API Monitoring and Threat Detection:
- Utilize AI-driven integrations for advanced behavior analysis, monitoring API traffic patterns, and quickly identifying anomalies that could indicate a security threat.
Understand Secure API Consumption:
- Thoroughly understand the security measures of any third-party APIs integrated into your systems. This includes their authentication process, data handling practices, and unknown vulnerabilities.
Regular Updates and Compliance:
- Continuously monitor and update security measures to address emerging threats. • Implement best practices for security, perform regular audits, and adhere to global regulations such as GDPR and HIPAA to ensure compliance.
Final Thoughts
APIs are never truly 'finished'. So, should your API Management Solution. By fostering a secure digital environment, these solutions allow you to safeguard your APIs, protect sensitive data, and uphold the trust of your users in the digital marketplace.
Astera API Management solution, with its built-in security framework, provides a single, intuitive, and integrated environment that goes beyond API management. Its one-stop platform offers comprehensive authentication, access control, and continuous monitoring tools, ensuring your APIs are secure and efficient.
Standardize your enterprise-wide APIs. Try a Free 14-day trial!
References
https://cloud.google.com/blog/... prominence
https://www.softwareag.com/en_... https://tyk.io/blog/what-is-ap...
https://content.salt.security/... https://www.perforce.com/blog/...
https://github.com/OWASP/API-S... management.md
https://kpmg.com/kpmg-us/content/dam/kpmg/pdf/2023/001355-
https://www.techtarget.com/sea... practices
https://www.forbes.com/sites/f... from-the-api-economy/?sh=72a9c46e4900
Post a comment